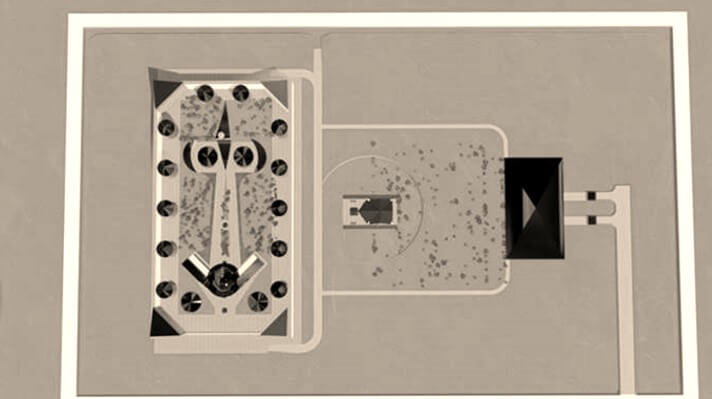
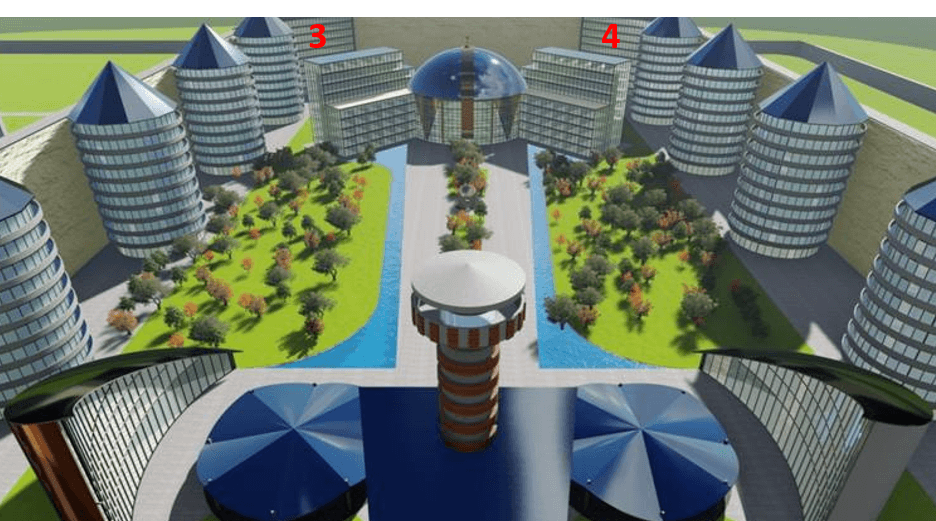
Boundary of Safe Building
Boundary of Safe Building
- After reaching the borders of the building (1), pedestrian and vehicle entrances are taken under control (2) and authorized.
- Physical tracking information such as the authorization stages and the tracking of the vehicle or pedestrian entering the interior, with whom and for what purpose until the exit, etc. are recorded.
Pedestrian and Vehicle Entrances of the Secure Building
1- Authorization of in-house vehicles,
2- Registration and tracking and transportation of vehicles and pedestrians outside the institution from the first border entrance to the last point with physical escort or electronic systems,
3- All information is given to the visitor at the entrance, and authorizations are approved by the visited authority.
Evacuation of the Safe Building
Damage Assessment of Safe Building
It is planned to carry out the security control of the building, physical damage and electronic damage detection at intervals to be determined by the protocol and after the attack.
Updating the System
The building's cables, wireless networks, closed lines are the living parts of the building and are protected.
All ventilation, sewerage, etc. connected to the building. Points that enter the inanimate part of the entire building, but which can be used by the enemy, have been isolated and taken under control.
EVACUATION
There are evacuation action plans for each against nuclear, biological, chemical and conventional attacks, as well as natural disasters. In the evacuation action plans, an action plan for crypto and electronic evacuation is provided simultaneously with the evacuation of people in the building. In the event of an attack on the protected facility, a 3rd eye action plan has been prepared so that the persons, troops and facility that will take physical action against the facility can be monitored by another facility.
CYBER SECURITY
The top floor of the triangular towers in the four corners is the cyber security towers.
- Activation of the warning system against cyber attacks - Initiation of counter-attack by the building cybercriminals - Securing electronic information against incoming attacks - Simultaneous closing of the attack angle.
Safe Rooms
It is secured electronically and physically in meetings or in case of attack. It has been determined and planned to authorize the people who will enter the safe rooms in normal times and under attack, and to divide the safe rooms into sections when necessary. It has been ensured that the personnel who will enter the safe room are kept in their own section.
LISTENING AND WATCHING
- Depending on the size of the building or facility, external surveillance and remote listening are prevented.
- It is important that surveillance and audio communication from the building to the outside remain open.
NIGHT DEFENSE-EVOCATION
- It is the night defense and evacuation of the building, with or without light.
- In the dark, when the faraday cage is operated, defense, evacuation, evasion, in case no light device works, are guaranteed. (National Seed Banks, Nuclear Facilities, Central Bank)
- The security of the product stored in the facility and the facility is ensured separately. It is planned to transfer the stored product, to destroy or render it unusable when necessary, and to save some of it by determining priorities.
- Heads of State, scientists and critical personnel are primarily secured.
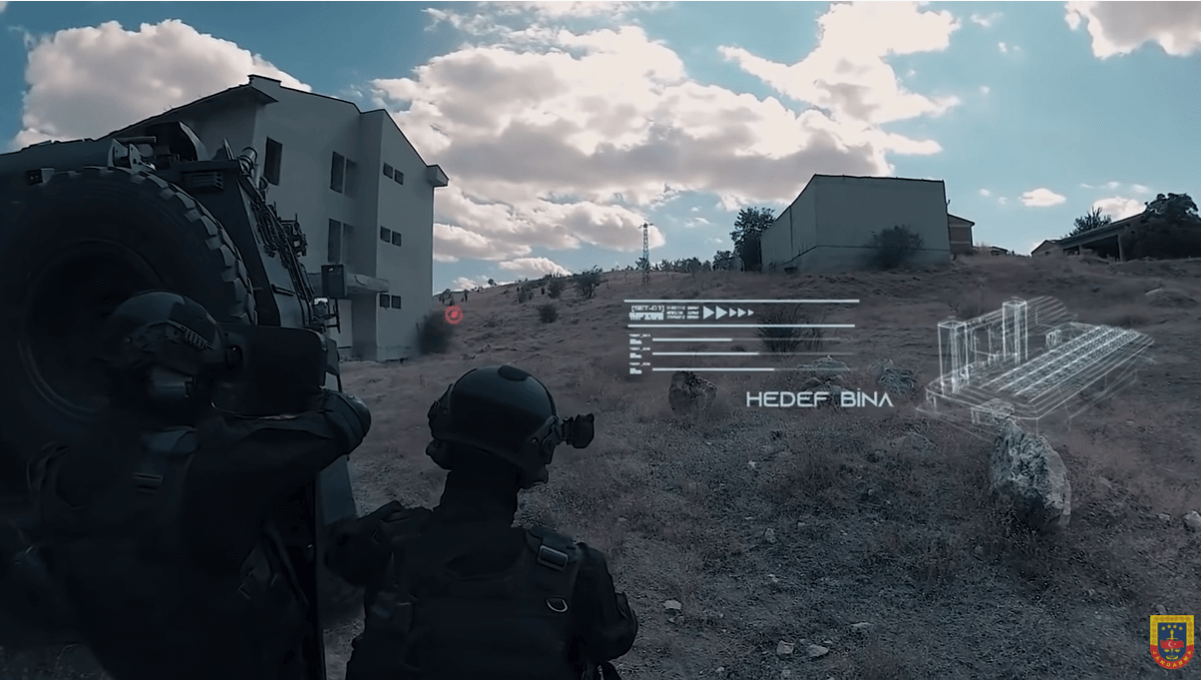
- For the operational units, a rapid troop shift operation is carried out for the execution of the first operation. It is planned to establish a mobile headquarters on the operational line, where electronic and physical security is provided.
RECONSIDERING A SHARED BUILDING
In the event that the high-security building cannot be protected and gets out of hand, it is to ensure the security of the electronic systems that were previously created in the building and will help during the operation and the operation teams to be used in the physical infiltration operation, and to support the operative units through maps. The efficient use of logistics and material in long-term stranded situations such as a nuclear attack is to keep communication with foreign troops open.